Describe the Following Security Considerations of Using the Internet Encryption
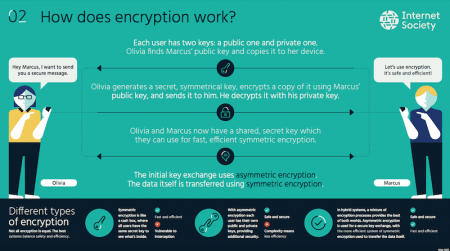
The most popular encryption scheme based on elliptic curves is the Elliptic Curve Integrated Encryption Scheme ECIES which is included in ANSI X963 IEEE 1363a ISOIEC 18033-2. A private key which is not shared decrypts the data.
Symmetric encryption uses a single password to encrypt and decrypt data.
. Using secp256k1 with JOSE and COSE This section defines. Web security scans should be performed on a schedule and after any change or addition to your web components. Which of the following are security dangers to using the Internet at work.
- Internal security labels. Two main types of transformation form the basis of IPsec. This document describes the use of authenticated encryption algorithms with the Encrypted Payload of the Internet Key Exchange version 2 IKEv2 protocol.
Security considerations for use of the first three algorithms are in Security considerations for use of the last algorithm are in. Data encryption options for. Encryption message by using DES.
There are a number of free tools on the Internet that you can use to measure how secure your website is. Those tools can be helpful for a brief review but they wont detect all the possible security flaws of your site. Safety and Security Considerations.
Use a public key encryption email standardlike SecureMultipurpose Internet Mail Extensions SMIME. It turns data into cipher text. The proposed system can be divided as the following steps.
Full PDF Package Download Full PDF Package. Some of the top considerations for implementing secure backup and recovery are-. Storing encrypted passwords in a.
The Store password using reversible encryption policy setting provides support for applications that use protocols that require the users password for authentication. Make the service vendor responsible for application security through contractual terms. The Spectrum of Encryption.
These two algorithms are the Advanced Encryption Standard AES in GaloisCounter Mode AES. This paper is organized as follows. 2 CMS Security Considerations.
Check all of the boxes that apply. Which of the following statements describe encryption. There is greater potential for data loss.
It provides security and authentication at the IP layer by transforming data using encryption. Check all of the boxes that apply. Asymmetric encryption uses two keys for encryption and decryption.
Cyber crime impacts your business by hacking your website. IPsec is performed inside the IP module and it can be applied with or without. One of the primary steps in a quantitative risk analysis is.
However the global encryption policy landscape is fracturing with different countries pursuing different approaches to encryption through both legal and technical means. 36 Full PDFs related to this paper. The protection can include confidentiality strong integrity of the data partial sequence integrity replay protection and data authentication.
Use encrypted connection strings instead. Encryption is widely used in systems like e-commerce and Internet banking. Information must secured and requires special handling - Need-to-know controls.
The use of two specific authenticated encryption algorithms with the IKEv2 Encrypted Payload is also described. A public key which is shared among users encrypts the data. A short summary of this paper.
One must prevents users from seeing information that they do not specifically need to know. This requires the senders and recipients email clients to all support the same standard and generally it wont work with browser-based webmail clients. The software should take steps to avoid disclosing the decrypted data except to the necessary and authorized recipients.
Embedding encrypted image by using LSB. Embedding encrypted message by using LSB in cover image. Role-based access control lists for all backup and recovery operations.
Chapter 19 IPsec Overview The IP Security Architecture IPsec provides cryptographic protection for IP datagrams in IPv4 and IPv6 network packets. The discussion does not include definitive solutions to the problems revealed though it does make some suggestions for reducing security risks. Note that these algorithms are already present in the IANA JSON Web Signature and Encryption Algorithms registry and so these registrations are only for the IANA COSE Algorithms registry.
The Authentication Header AH and ESP. Section 2 describes the proposed system. Do not expose user passwords in code or in external files ie.
Encryption is a critical tool to protect sensitive information prevent cybercrime and digital fraud and authenticate digital transactions. File with connection strings that are used by the application. This means that if you are using the virtual device and your Azure subscription is compromised the data stored on your virtual device is also susceptible.
Website Security Consideration Websites are always to prone to security risks. This section is meant to inform application developers information providers and users of the security limitations in HTTP11 as described by this document. It has become easier for the average site owner to get online quickly with the use of an open source content management system CMS such as WordPress Magento Joomla or Drupal.
The virtual device is secured through your Microsoft Azure subscription. Good passwords are essential to. A password is a string of characters used to authenticate a user to access a system.
Keep the following security considerations in mind when you use the StorSimple virtual device. Authentication of the users and backup clients to the backup server. Prefer using Windows Authentication for application service accounts that connect to your SQL Server instance instead of Mixed Mode usernamepassword.
They provide data integrity data origin authentication and anti-replay services. Security and Practical Considerations When Implementing the Elliptic Curve Integrated Encryption Scheme. Encryption cover image by using SCAN method.
Review the need for encryption of stored and transmitted application data. Describes the best practices location values and security considerations for the Store passwords using reversible encryption security policy setting.
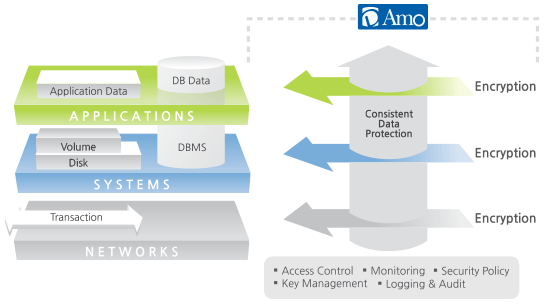
Database Db Encryption Everything You Need To Know
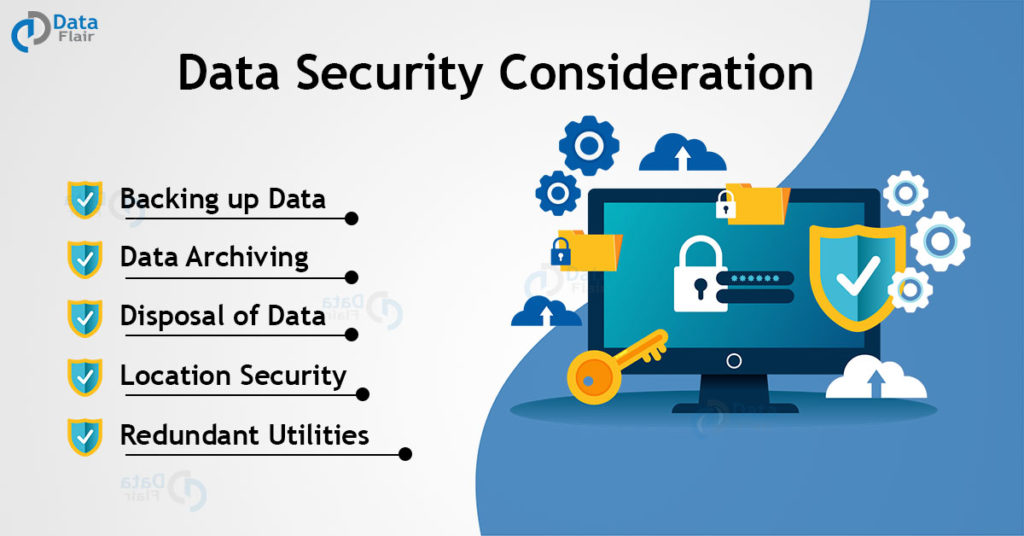
Data Security Considerations In Cyber Security Dataflair

Chapter 6 Information Systems Security Information Systems For Business And Beyond

Guidance On Cloud Service Cryptography Itsp 50 106 Canadian Centre For Cyber Security
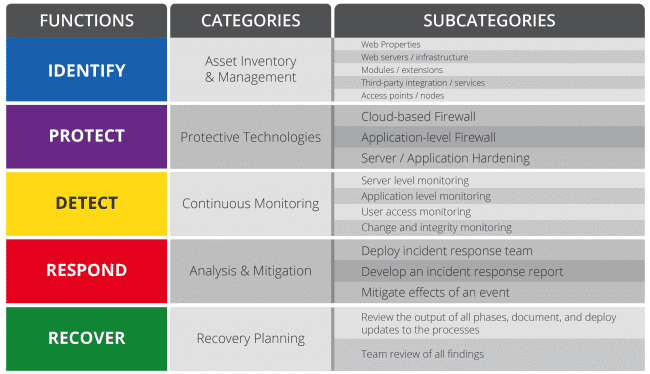
Website Security How To Secure Protect Your Website

Website Security How To Secure Protect Your Website
Server Security Explained What Is Server Security Avast

Guidance On Cloud Service Cryptography Itsp 50 106 Canadian Centre For Cyber Security
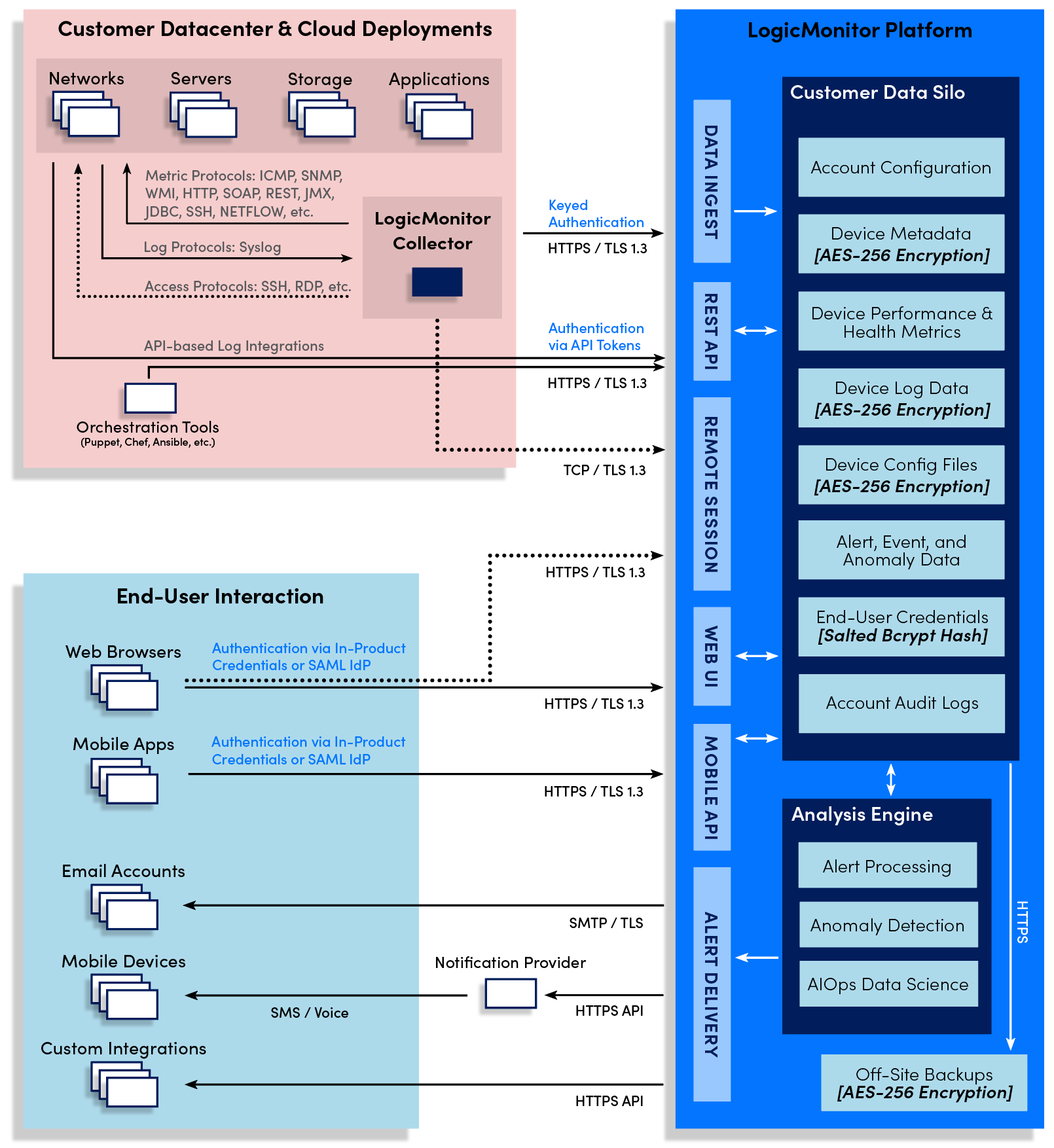
Logicmonitor Security Best Practices Logicmonitor
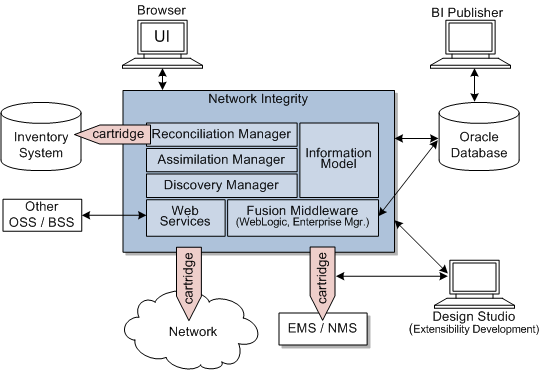
Network Integrity Security Overview

Securely Extend And Access On Premises Active Directory Domain Controllers In Aws Aws Security Blog
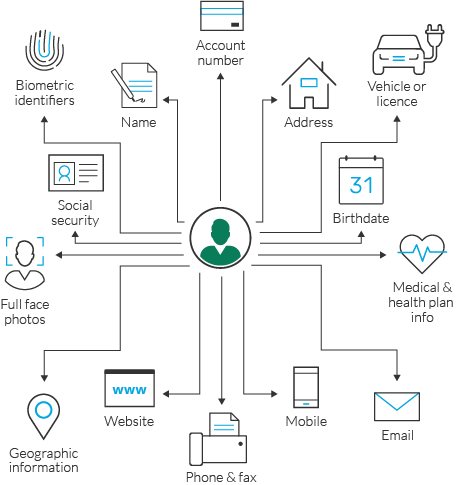
What Is Personally Identifiable Information Pii Data Security Imperva
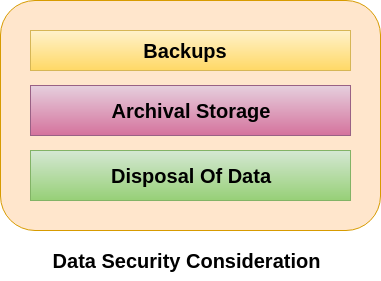
Data Security Considerations Javatpoint
7 Security Factors To Consider When Choosing A Web Host Hashed Out By The Ssl Store
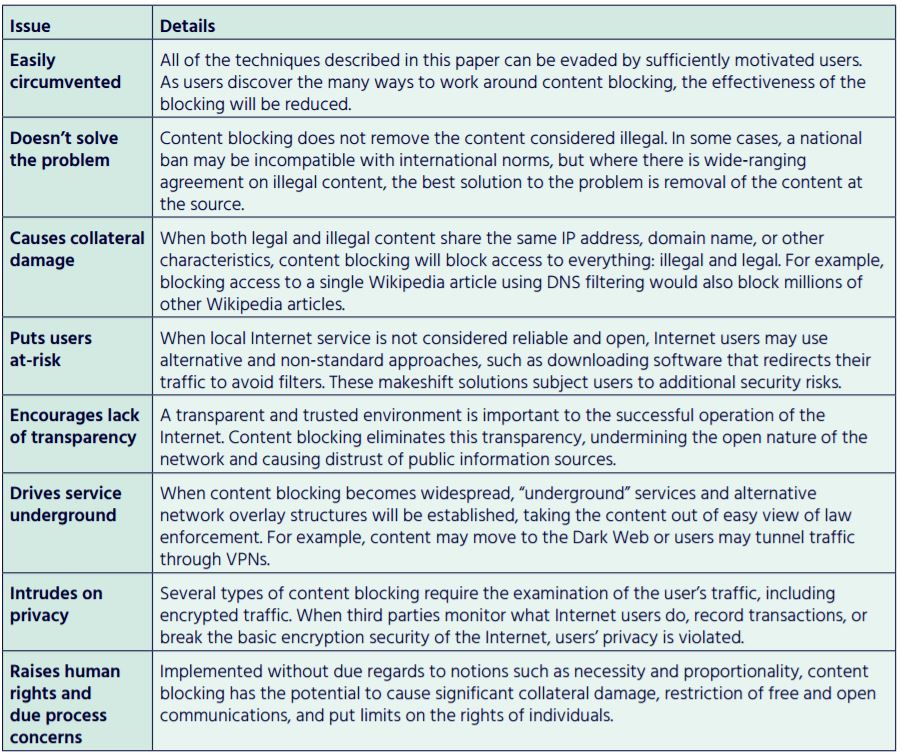
An Overview Of Internet Content Blocking Isoc Internet Society
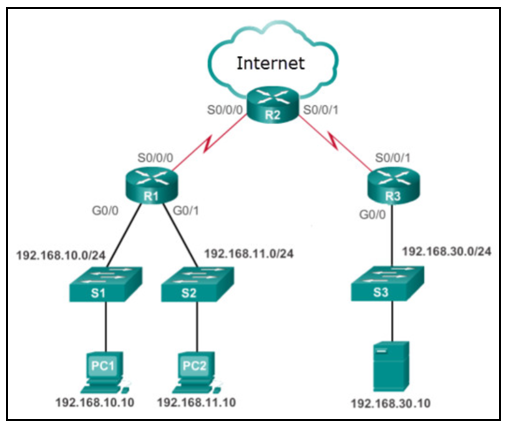
Ccna 3 V7 Modules 3 5 Network Security Exam Answers
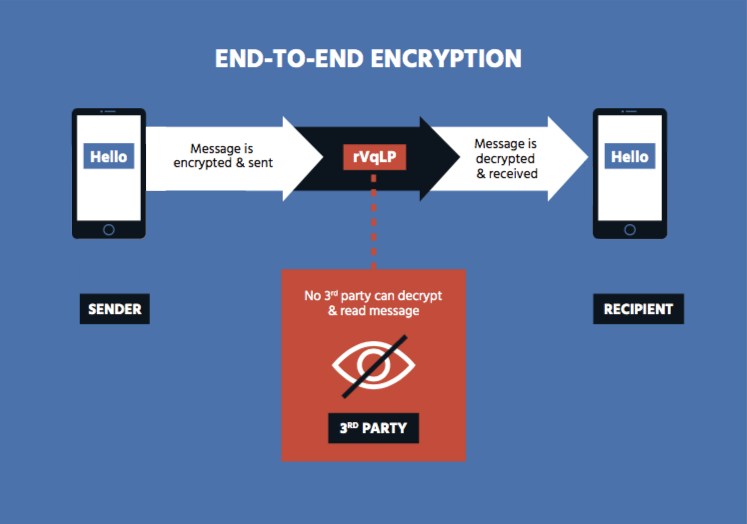
Encryption Brief Internet Society

Guidance On Cloud Service Cryptography Itsp 50 106 Canadian Centre For Cyber Security
Comments
Post a Comment